Ryuk Ransomware
8 January 2021
SafeAeon Inc.If you follow cybersecurity trends, you must be well aware of the threat of ransomware on SMBs (Small and Medium Businesses). If your organization is attacked by the ryuk strain of ransomware, you are likely to pay four times of average ransom. So let’s discuss the potentially most lethal and active family of ransomware in the past two years.
What is Ryuk and its origin?
Ryuk is a strain of ransomware, which is specially used for targeting big organizations and demanding very high ransoms. Its name comes from anime and manga series “Death Note,” where ryuk is the name of Demon of Death. Ryuk is operated by Russia based criminal group called “Wizard Spider.” After analyzing and comparing its code with ‘Hermes Ransomware,’ it is believed that ryuk was developed from the source code of ‘Hermes’ and continuously updated to make it more lethal. It first appeared in August 2018 when it attacked at least three big organizations and received the amount believed to be around $600,000. Since its first appearance, it has a net gross of over $3,700.000.
How Ryuk gains access?
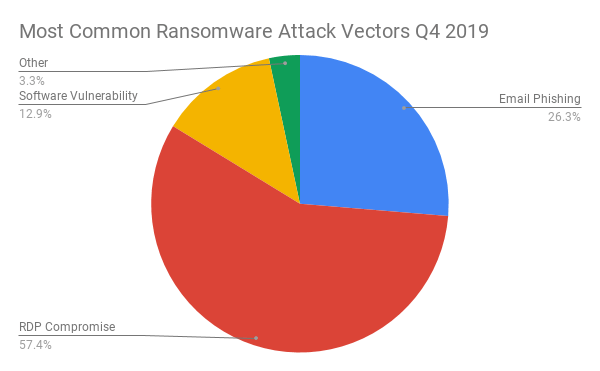
Like any other ransomware, ryuk’s favorite attack method is through RDP compromise or phishing mail. According to Coveware, RDP compromises account for 57.4% and phishing mail for 26.3% of ransomware attacks. Attackers generally use brute-force to compromise misconfigured RDP ports. Even if they are protected, due to the mass availability of RDP credentials over the internet for very cheap as $30 per IP, it makes these attacks very economical to attackers, and they will continue to exploit. But unlike other ransomwares, which use mass targeting, ryuk is used for specific targeting.
How Ryuk Works?
Ryuk doesn’t infect or spread completely on its own; instead, it uses ‘Emotet’ and ‘TrickBot’ banking trojans to distribute. Generally, it starts with ‘Emotet,’ which makes the initial infection on the endpoint, then it spread throughout the network as well as launch its own malspam campaign from the infected endpoint, sending additional malware to other users on the same or different networks.
Malware dropped by ‘Emotet’ is another malware called ‘TrickBot,’ which is capable of stealing network credentials and spreading all over the network. Finally, ‘TrickBot’ drops its payload, which is ryuk to encrypt and deny access to all valuable resources. Ryuk can be dropped by using’ TrickBot’ only.
Ryuk Top Victims
Tribune Publishing: Dec 2018, Ryuk caused publishing and delivery disruption to several major US newspapers whose printing center was operated under Tribune Publishing. Many print editions like Chicago Tribune, Lake County News-Sun, Post-Tribune were published without classified and death note.
Florida State: In the Summer of 2019, two US cities of Florida paid around 1.1 million dollars as ransom. Riveria Beach and Lake city paid $600,000 and $500,000, respectively. The city of Riveria beach was so badly affected that essential services like 911 and water supply was brought to a halt.
Emcor: Mar 2020, a Fortune 500 organization that specializes in mechanical and electrical construction services, also became a victim of ryuk ransomware. It has to shut all its IT infrastructure to deal with ransomware. Even though details of the attack are not public, but the ransomware message was visible on the company website for almost three weeks.
Durham, North Carolina: Mar 2020, around 1000 of Durham county computers were hacked after one of their employee of county clicked on infected mail. Due to the proper backup system in the palace, the country was rescued from large financial as well as reputational loss, but still, a lot of time and efforts were on the palace to recover all the systems.
People also read about: Latest Ransomware Trends














