What is Penetration Testing-as-a-Service (PTaaS)?
"Simulation of a real-world cyber attack!"
Penetration Testing, also known as Pen Testing, is a simulated cyber attack on a computer system or network to identify vulnerabilities and weaknesses. SafeAeon's Penetration Testing-as-a-Service (PTaaS) uses the same tools, techniques, and methodologies as malicious hackers to simulate a real-world attack on your IT infrastructure. Unlike a real attack, our PTaaS is conducted in a controlled environment, allowing you to discover and fix problems before they can be exploited by attackers. Our PTaaS service produces a comprehensive report that not only identifies security vulnerabilities but also provides recommendations on how to improve your overall security posture. Trust SafeAeon's PTaaS to keep your network secure and protect your business from real-world cyber attacks.
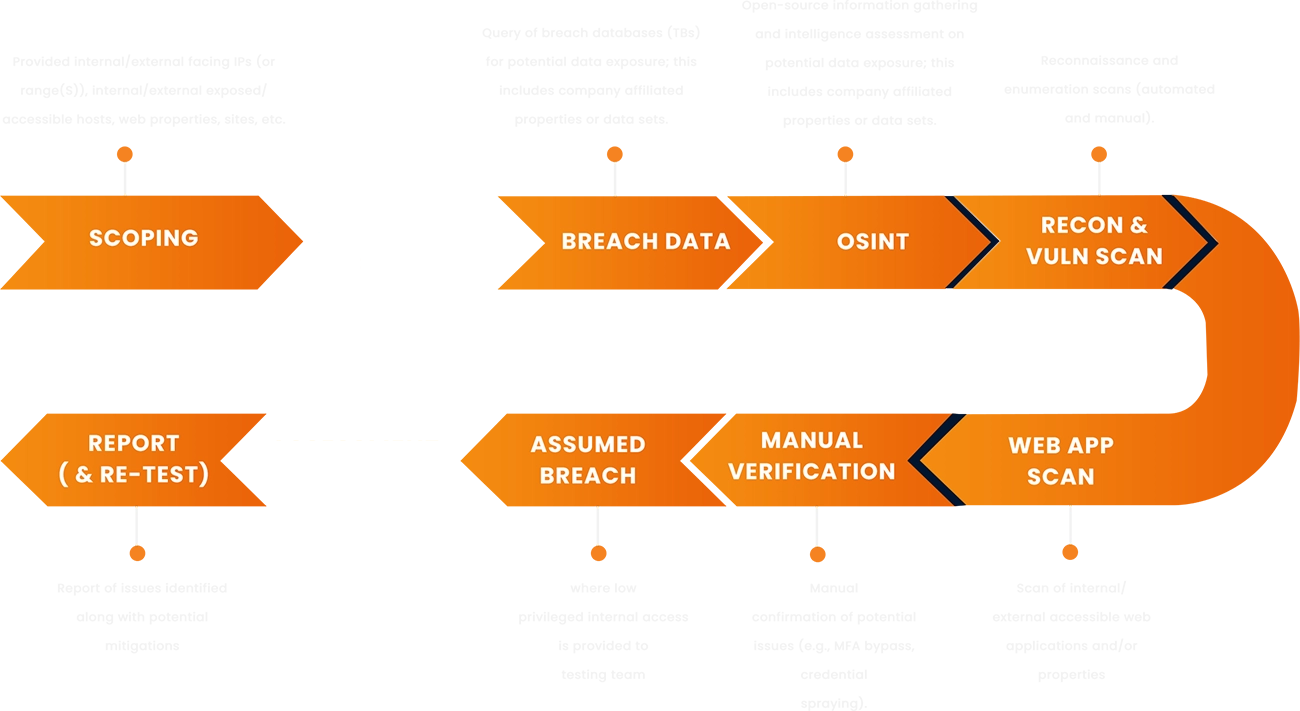
SafeAeon PTaaS Approach
Types of Penetration Testing-as-a-Service We Provide
SafeAeon's team of penetration testing service providers performs pen testing remotely or on-site as needed. Our full range of Penetration Testing-as-a-Service ensures that you have visibility to potential gaps and weaknesses throughout your IT environment and fix them before hackers!
SafeAeon’s Wireless Pen Testing Areas
Social Engineering Assessment
During SafeAeon’s Social Engineering Audit, SafeAeon tests electronically (computer based) and phone based.

The testing gathers open source information prior to the engagement through online information gathering. The testing impersonates sources of authority and use a variety of techniques such as:
-
Spear Phishing in conjunction with the simulated exploitation of the endpoint
-
Phone based social engineering including Caller ID and SMS spoofing along with Vishing exercises (Voice Phishing)
-
Social engineering tasks by randomly distributing special USB devices with simulated malware
-
Continuous e-learning user cybersecurity protection education
All services come with comprehensive reporting, user tracking and event classification.
Frequently Asked Questions About PTaaS
Penetration Testing, in contrast, is a more comprehensive approach that includes identifying vulnerabilities and exploiting them using real-world methods. It also helps identify the potential impact of discovered vulnerabilities on business operations and provides recommendations to address those weaknesses.
Why Do You Need Our Services
SafeAeon's 24×7 SOC operates ceaselessly to watch over, identify, and counter cyber attacks, ensuring your business remains resilient and unharmed
24/7 Eyes On Screen
Rest easy with SafeAeon's continuous vigilance for your IT infrastructure. Our dedicated security analysts ensure prompt threat detection and containment.
Unbeatable Prices
Access cutting-edge cybersecurity products through SafeAeon's unbeatable deals. Premium solutions at competitive prices for top-tier security.
Threat Intelligence
Stay ahead with SafeAeon's researched Threat Intelligence Data. Clients enjoy free access for informed and proactive cybersecurity strategies.
Extended IT Team
Seamlessly integrate SafeAeon with your IT team. Strengthen controls against risks and threats with expert recommendations for unified security.
Ready to take control of your Security?
We are here to help
Reach out to schedule a demo with our team and learn how SafeAeon Penetration Testing-as-a-Service can benefit your organization