10 November 2023
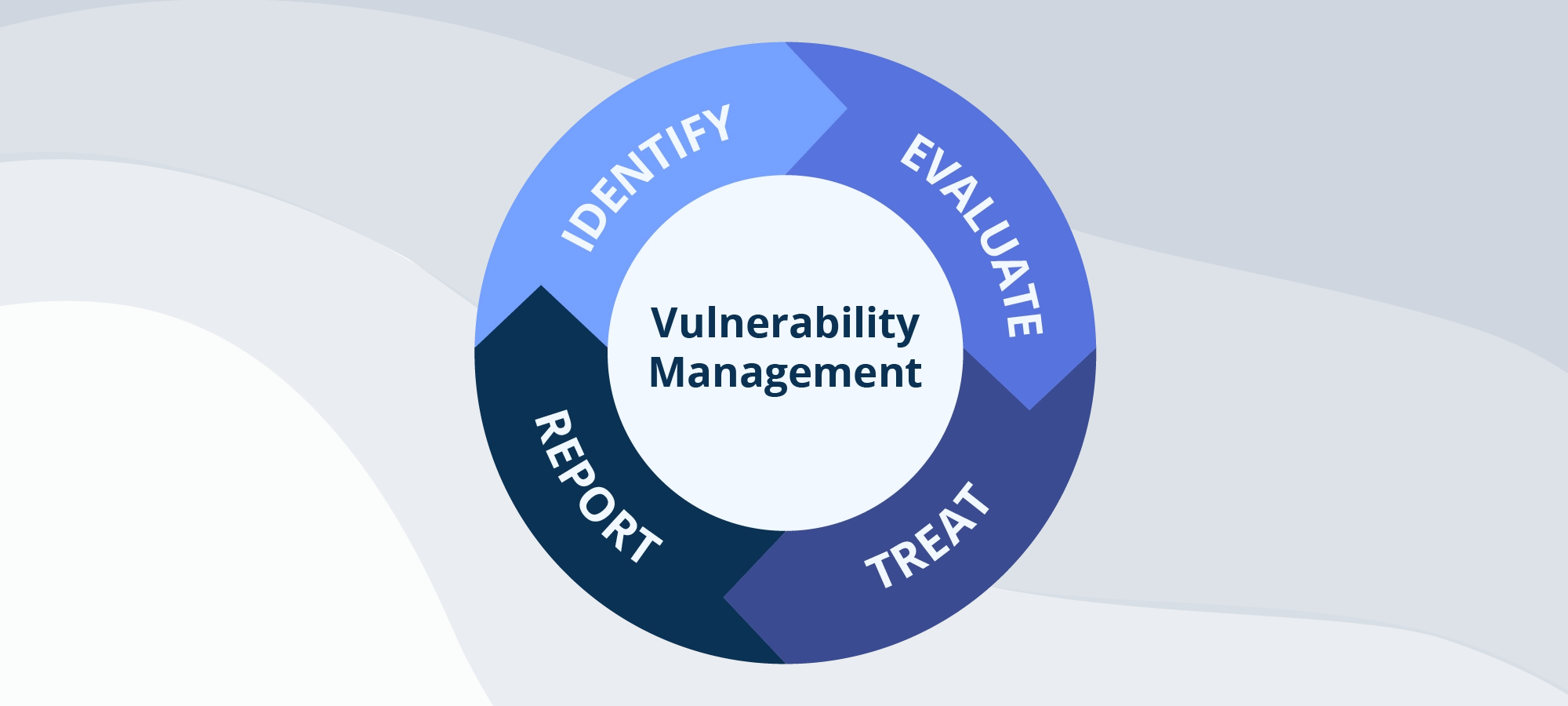
SafeAeon Inc.Let’s start by asking ourselves a question; what comes first to our mind from strengthening Cybersecurity? Of course, it’s about preventing malicious threats in our digital space or working on the vulnerabilities. Isn’t it? One such renowned system known for strengthening cybersecurity is Vulnerability management (VM). It involves identifying, assessing, mitigating, and documenting security flaws. These steps are crucial for business operations, web applications, and systems along with their software. This critical process must be ongoing. It addresses the constant addition of new systems to networks and changes to existing systems and applications. It also deals with the emergence of new security vulnerabilities.
Attackers often exploit known weaknesses in browsers, operating systems, and third-party software. They use these weaknesses as an initial tactic to compromise systems. Proactively identifying and remedying such security gaps is fundamental. It's a key part of maintaining the integrity of any cybersecurity strategy.
How Advanced Vulnerability Management Takes Edge Over Traditional Vulnerability Management?
Enhanced vulnerability management fuses the processes of identifying, evaluating, and rectifying vulnerabilities into a cohesive, ongoing cycle. It broadens the horizon for threat detection, encompassing a wider array of security risks such as misconfigurations, omissions in settings, and unusual security deviations, in addition to traditional software vulnerabilities.
This approach reinforces the notion that managing vulnerabilities should be a perpetual endeavor, enabling organizations to swiftly apply fixes, avert potential threats, and fortify defenses against cyber incursions.
By integrating the core aspects of traditional vulnerability management and infusing them with additional depth and robustness, it offers a more comprehensive and dynamic defense mechanism for an organization's digital infrastructure. Utilizing this approach allows you to:
- Gain full oversight of your digital environment
- Enhance the testing capabilities for intricate and evolving web applications.
- Boost defenses against phishing, various social engineering tactics, and irregular user activities.
- Employ ethical hacking techniques to gauge the aggregate risk and improve the focus of your corrective actions.
A Guide To Build Step-By-Step Unified Vulnerability Management
Find all of your IT assets for full network visibility
Identifying all of an organization's IT assets is a key part of effective vulnerability management. This covers everything in your network, from workstations and routers to switches and routers.
What Does It Really Mean?
As part of this process, you will make a full and up-to-date list of all the devices that are tied to your company's network. Attackers often go after old or ignored devices, which makes them a security risk. You can't lock it up if you can't see it. Even forgetting about one device can cause huge security holes. As a result, having complete network transparency is important and forms the basis of a strong vulnerability management strategy. This openness is important for understanding and improving the security of your company.
How do you do it?
Usually, thorough scanning tools are used for asset discovery. These tools look at and list all of your infrastructure's hardware. These tools are made to look through your network and find all of your IT assets, such as computers, routers, servers, and switches. For this, it is highly recommended that you use accurate and reliable accounting tools.
Why is it important?
It's not better to not know about hacking. You can't protect things you don't know about. Asset discovery makes sure that every part of your network is inspected for security flaws. So, no device is left open or unaccounted for in your IT world. This lowers the chance that attackers will take advantage of gadgets that aren't protected.
A clear picture of your network's assets helps you keep an eye on and control its performance better. This makes your tech resources last longer and work better.
2. Using quantitative analysis to figure out your security posture
The range of your organization's possible weaknesses is shown by its complete set of assets and network devices. The next step in advanced risk management is to evaluate and measure this exposure.
What does this mean?
In this step, you'll figure out how much risk your company might be by carefully looking at each part of the network and the holes they might have. To understand your attack surface quantitatively, you need to find and rank the network's weakest and most important places. Using numbers to show your attack surface also has many benefits, such as making the risk management process easier and more clear.
How does this get done?
For quantification, you usually need a specialized, data-driven tool that can collect, analyze, and rate risk data. This tool should use a complex program to turn the wide and complicated attack surface into a figure that is easy to understand. It needs to give a full assessment of each device's security readiness so that the general security posture is clear.
Why does it matter?
Setting a number for your attack area makes it easier to understand all of your network's weaknesses. It helps people make clear, targeted choices about what to do to fix things. By keeping an eye on changes in the attack surface's numbers, you can figure out how well your defenses are working and make them better.
Simplifying your risk profile to a single number can make conversations with stakeholders a lot better. This way, you can give them a clear picture of the risk without having to write long, complicated reports.
3. Finding Security Risks Other Than Software Bugs
After making a list of all of your assets and devices, the next step is to find any possible weak spots in your network.
What Does It Do?
As part of this process, security holes and other threats are scanned for. A built-in scanner that uses a huge library of security holes is usually used to do the scans. Even though software bugs are a known security risk, they are only a small part of the bigger picture. Hackers today also use problems like wrong settings, strange operations, the exposure of important assets, and policy deviations from security to get into networks.
How Do You Do It?
- Assets are scanned regularly to find any security holes by looking at the software and systems on the devices.
- The scans should find more than just bugs in the software. They should also find incorrect settings, strange behavior patterns, and violations of security rules. This way, they should find all possible ways to attack.
- It's important to use an advanced scanning tool that can find these kinds of risks quickly and accurately while also lowering the chance of getting false results.
What's The Need For It?
- Figuring out your weaknesses is the first step to fixing them.
- Correct identification lets problems be properly prioritized and effectively fixed.
Compliance standards often say that vulnerability checks need to be done regularly.
4. Intelligent Prioritization of Risks & Vulnerabilities beyond CVSS
There are many vulnerabilities, and not all of them need the same amount of attention. While some weaknesses may require a lot of work to fix, they may not make the network any safer overall.
What Does It Do?
It's the process of figuring out which security problems need to be fixed first by figuring out how bad they are and how they might affect the business. This process is automated by Advanced Vulnerability Management (AVM), which frees up your resources to do other things. This method makes sure that you deal with the most important risks first, taking into account the business situation and how likely it is that they will be exploited. This reduces the area that could be attacked.
How Do You Do It?
Sort weaknesses into levels like "critical," "high," "medium," and "low priority" in a planned way. This classification makes sure that the worst flaws are fixed quickly so that they can't be used against the system. Use risk ranking tools that look at different types of data to help you decide the order of remediation, but if you can, choose an all-in-one solution that takes care of all aspects of vulnerability management.
What's The Need for It?
- New bugs that take advantage of old security holes can be very dangerous. A dynamic severity scoring system can help you set priorities more wisely and lower risks more effectively.
- Using information about weaknesses that are already out there, like information on public exploits and past attacks, makes sure that the most dangerous ones get fixed right away.
Conclusion
Unified vulnerability management stands as a cornerstone in fortifying cybersecurity. It consolidates the detection, evaluation, and remediation of vulnerabilities into a streamlined, ongoing process. By embracing this comprehensive approach, organizations can not only anticipate and defend against a range of cyber threats but also enhance their overall security posture. Unified vulnerability management is more than just a defensive tactic; it's a strategic advantage that empowers businesses to operate with confidence in an increasingly digital world. Looking out for professional experts to help you with Unified vulnerability management then SafeAeon is provenly the best choice.














