08 February 2024
SafeAeon Inc.Imagine joining a Wi-Fi network that looks like it's familiar, but you don't know that you just gave your private information to a digital copy of yourself. This scary situation, called an "evil twin attack," is a smart way for hackers to get into systems and steal information. Only in 2023, phishing attempts (including evil twins) were responsible for 38% of all data breaches. This shows how important it is to understand this sneaky threat.
So, how do evil twins work? Wi-Fi hotspots often impersonate genuine networks, often adopting similar names and exploiting vulnerabilities in public Wi-Fi networks. When people connect without realizing it, their data, like login credentials, banking information, and personal messages, flows through the attacker's server without their knowledge. This puts them at risk for many things, including:
- Data theft: Private data like credit card numbers and passwords is easy to steal and use against you.
- Malware Injection: Attackers can put harmful software on your device, which makes it less safe and less useful.
- Man-in-the-Middle Attacks: The attacker listens in on your internet conversations and changes the data that is sent back and forth.
The results can be very bad. Verizon released a study in 2022 that said phishing-related data breaches cost an average of $4.9 million. This shows how much money these attacks cost. People and businesses can lose more than just money. They can also suffer from damage to their image, identity theft, and problems with their operations.
Don't worry, though! Being smart is your best defense. Learn how to spot the clear signs of a fake network with this in-depth guide to evil twin attacks.
- Use basic security steps to keep your data safe.
- Safely and securely use public Wi-Fi.
- Give yourself the tools you need to fight this threat.
Let's bring attention to evil twin strikes and protect your online privacy in a world that is becoming more and more linked.
How to Spot Evil Twin Wi-Fi Attacks?
Cyberattacks called "evil twin Wi-Fi" are very advanced and look like real public Wi-Fi networks. Here is a breakdown of how these attacks are put together:
Step 1: Pick the Best Place to Be
Attackers go after places like airports, libraries, and bars that are known for having free Wi-Fi that a lot of people use. There are usually a lot of Wi-Fi networks in these places, which makes it easier for a fake network to fit in without being seen.
Step 2: Pretending to be a real Wi-Fi network
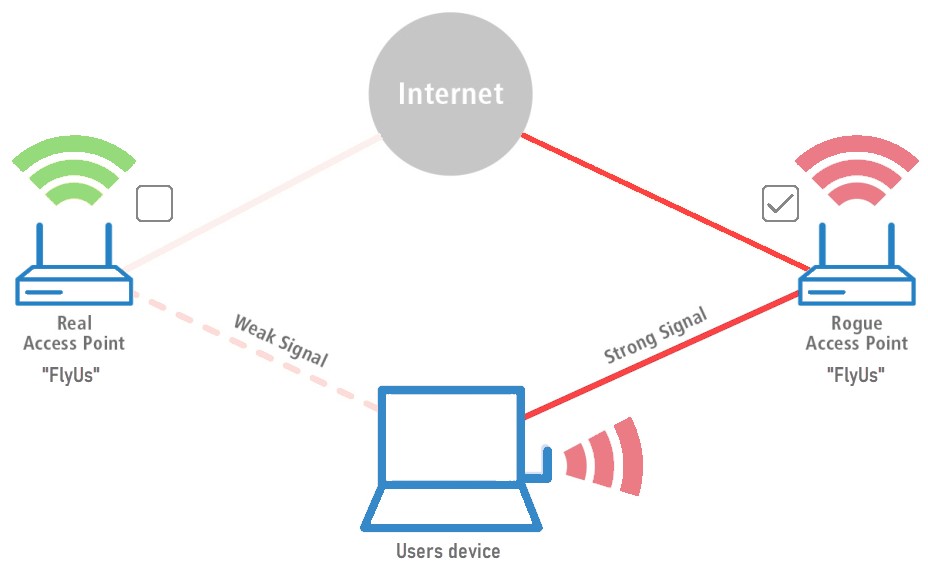
The offender finds the Service Set Identifier (SSID) of a real network and uses it to make a new Wi-Fi access point with the same SSID. Several types of devices, including smartphones, laptops, and specialty gear like a Wi-Fi Pineapple, can be used to make the fake network reach further. Devices have a hard time telling the difference between real and fake networks because they look so much alike.
Step 3: Getting people to join the fake network
Attackers boost the broadcast of their network by moving closer to people who might be targets. People often choose the stronger but more dangerous network because of this, and their devices will sometimes instantly connect to it.
Step 4: Making a fake login page
A lot of public Wi-Fi networks have a "captive portal" that users have to use to log in. Attackers take advantage of this by making a copy of the login page and using it to steal users' passwords. Once attackers have this information, they can get into the network without permission and maybe even get into victims' devices.
Step 5: Getting personal information
All user action goes through the attacker's system once they are connected to the bad network. Being in this "man-in-the-middle" situation lets them watch and steal any data being sent, such as banking information and social media activity. People who log in to personal accounts run the risk of having their credentials stolen, especially if they use the same passwords on more than one site.
Example of an Evil Twin Attack
Picture someone sitting down at their favorite coffee shop, getting ready to enjoy a coffee while surfing the web. They've used the café's Wi-Fi before without any problems, so they don't think twice about connecting again. They didn't know it, but someone nearby had started an evil twin attack by making a fake Wi-Fi network that looked exactly like the real café's SSID. The attacker's fake network sends out a stronger signal when it is close to the target, tricking them into connecting to it even though it is not secure.
When someone uses online banking to send money to a friend, they don't know they're open to prying eyes because they don't have a VPN. A VPN would encrypt their data and keep it safe. The attacker can get their account information from the fake network. The breach isn't noticed until someone sees deals that weren't supposed to be there, which costs them money.
How Dangerous Evil Twin Attacks Are?
Evil twin attacks are dangerous because they can let attackers get into private devices and take over secret data. Hackers can get banking information, login information, and even put malware on your computer. Because these attacks do what you expect them to do, which is give you access to the internet, there aren't many obvious signs of wrongdoing. People usually don't realize they've been hacked until they find out that someone else has done something or bought something in their name without their permission.
How to Protect Your Device From Evil Twin Attacks
To protect yourself from the dangers of harmful hotspots and evil twin attacks, you might want to do the following:
Choose Secure Connections: When you're in a public place, connect to a secure network instead of an open one. Networks that aren't protected don't have the basic security protocols they need, so they are a popular target for evil twin attacks. Hackers take advantage of the fact that most people don't know about these risks.
Personal Hotspots: Use your mobile hotspot to stay safer online while you're out and about. This makes sure you're on a network you can trust, which makes data leaks much less likely. Make sure you use a strong password to protect your hotspot.
Security Alerts: When you try to join a new network, pay close attention to any security alerts your device may send you. These warnings are meant to stop people from connecting to networks that could be dangerous. Ignoring these alerts could put you at risk for no reason.
Turn Off Auto-Connect: If you turn off your device's auto-connect feature, it won't instantly connect to known networks, which could include fake ones that look like real ones. When you choose networks by hand, you can look them over carefully before connecting, which gives you more control over network security.
Do not do anything sensitive on public Wi-Fi: To keep your risk as low as possible, don't do business or log into private accounts on public Wi-Fi networks. Hackers can get into these networks and steal information, so it's better not to log into personal accounts.
Turn on multi-factor authentication: This adds an extra layer of security by needing both a password and a secondary verification, such as a code sent to your phone, to access your accounts. This makes it harder for attackers to get to your personal information without your permission.
Prioritize HTTPS Websites: When you're on a public network, make sure that any website you visit uses HTTPS. This means that the contact between your browser and the site is safe and encrypted. Attackers will not be able to get to your info if it is encrypted.
Get a Virtual Private Network (VPN): By encrypting your internet data, a VPN protects you well against evil twins and other Wi-Fi attacks. Outsiders, including possible hackers, can't read your online activities because of this encryption. This keeps your info private.
You can make your defenses stronger against the complex threat of evil twin attacks by using these tips. This will keep your online experience safe and secure.
Conclusion
Evil twin attacks are a big problem in a world that is becoming more and more linked. These attacks use public Wi-Fi networks to trick users and steal their data. People are being tricked into connecting to malicious networks by these clever cyberattacks that look like real access points. To fight these dangers, education and raising awareness are very important. Users need to be careful, especially when they're in public places. They can do this by checking the security of the networks they connect to, using VPNs for protection, and keeping an eye on the networks they connect to. People can better keep themselves and their private data safe from hackers if they understand how evil twin attacks work. For more assistance, you can get in touch with SafeAeon today.














