Endpoint detection and response (EDR) - Core Functionality
4 October 2022
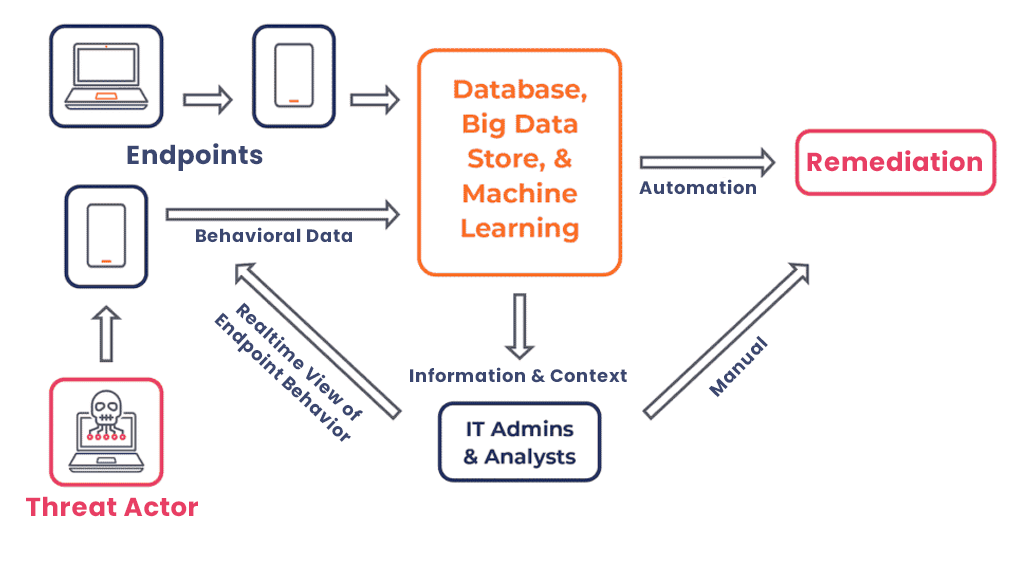
SafeAeon Inc.EDR (Endpoint Detection and Response) security solution detects threats across the company's network. It detects the entire lifecycle of the threat, providing insights as to what happened, how it got in, how far it has gone, what it is doing now, and the best possible action to take to contain the threat at the endpoint.
Key capabilities of EDR
Detection: This is a foundational capability of EDR. It does not matter if an advanced threat will attack. It will matter if it evades front-line defenses. With consistent file analysis, EDR flags offending files at the first sign of malicious behavior.
Containment: Once malicious files are detected, EDR must be able to contain the threat. Such malicious files aim to infect as much as processes, applications, and users as if not contained; Segmentation can also be a great defense within your data center to avoid advanced threats.
Analysis: After the detection and suppression of the malicious file. EDR solution should analyze the detection. If the file does not pass the first perimeter of the security, then it seems vulnerable and needs to be checked. EDR provides adequate incident review required to mitigate these issues and prevent future exploitation from the same threat.
Annihilation: Detecting, containing, and successfully investigating a threat is great, but if you cannot eliminate it, then basically, you continue, knowing that your system is compromised. That is not acceptable. EDR solutions can eliminate threats detected to the environment. EDR extends its capabilities to all connected devices, provides a consistent layer of security everywhere, and performs mitigation actions completely. If you cannot see it, you cannot protect it. Ultimately, it is necessary to understand that the best EDR solution combines the Endpoint Protection Platform and Endpoint Detection and Response capabilities. The true next-generation security solution for endpoints will provide the protective first line of defense against cyber-attacks on the endpoint. It will continuously monitor the environment, which will provide and manage security.
Detection: This is a foundational capability of EDR. It does not matter if an advanced threat will attack. It will matter if it evades front-line defenses. With consistent file analysis, EDR flags offending files at the first sign of malicious behavior.
Containment: Once malicious files are detected, EDR must be able to contain the threat. Such malicious files aim to infect as much as processes, applications, and users as if not contained; Segmentation can also be a great defense within your data center to avoid advanced threats.
Analysis: After the detection and suppression of the malicious file. EDR solution should analyze the detection. If the file does not pass the first perimeter of the security, then it seems vulnerable and needs to be checked. EDR provides adequate incident review required to mitigate these issues and prevent future exploitation from the same threat.
Annihilation: Detecting, containing, and successfully investigating a threat is great, but if you cannot eliminate it, then basically, you continue, knowing that your system is compromised. That is not acceptable. EDR solutions can eliminate threats detected to the environment. EDR extends its capabilities to all connected devices, provides a consistent layer of security everywhere, and performs mitigation actions completely. If you cannot see it, you cannot protect it. Ultimately, it is necessary to understand that the best EDR solution combines the Endpoint Protection Platform and Endpoint Detection and Response capabilities. The true next-generation security solution for endpoints will provide the protective first line of defense against cyber-attacks on the endpoint. It will continuously monitor the environment, which will provide and manage security.
Detection: This is a foundational capability of EDR. It does not matter if an advanced threat will attack. It will matter if it evades front-line defenses. With consistent file analysis, EDR flags offending files at the first sign of malicious behavior.
Containment: Once malicious files are detected, EDR must be able to contain the threat. Such malicious files aim to infect as much as processes, applications, and users as if not contained; Segmentation can also be a great defense within your data center to avoid advanced threats.
Analysis: After the detection and suppression of the malicious file. EDR solution should analyze the detection. If the file does not pass the first perimeter of the security, then it seems vulnerable and needs to be checked. EDR provides adequate incident review required to mitigate these issues and prevent future exploitation from the same threat.
Annihilation: Detecting, containing, and successfully investigating a threat is great, but if you cannot eliminate it, then basically, you continue, knowing that your system is compromised. That is not acceptable. EDR solutions can eliminate threats detected to the environment. EDR extends its capabilities to all connected devices, provides a consistent layer of security everywhere, and performs mitigation actions completely. If you cannot see it, you cannot protect it.
Ultimately, it is necessary to understand that the best EDR solution combines the Endpoint Protection Platform and Endpoint Detection and Response capabilities. The true next-generation security solution for endpoints will provide the protective first line of defense against cyber-attacks on the endpoint. It will continuously monitor the environment, which will provide and manage security.
Contact us today and learn how we can safeguard your organization and help secure your business.